Passwords are not generally stored in plaintext form.
crypt() is a one way hash function that expects a plaintext password and a salt value for input and then outputs a hash with the salt value prepended to it.
This hash is mathematically irreversible ,meaning that it is impossible to determine the original password using only the hash.
So if user wants to authenticate user will enter the password and then hash corresponding to that password will be generated ,and if the hash matches with the hash stored in file ,then user entered the correct password .In this way without storing the password in plaintext form we can have authentication here.
With this mechanism ,we can think of that the even encrypted password stored in the file is useful ,so we can have a dictionary attack here by hashing each word in the wordlist and compare it with the hash stored in the file ,so in this way we can crack the password.
Dictionary Attack program will just needs to read word from file ,hash each using the proper salt value and display the word if there is a match.
##Libraries used
'stdio.h' for the filestream operations
'unistd.h' for crypt() where crypt is a password encryption function ,it is based on Data Encryption Standard algorithm with variations intended to discourage use of hardware implementations of key search.
##method to print message
##Main Method starts:
Define the variables needs to be used
for this program to be executed we need mandatory two cmd arguements:
1. word list file path
2. hash which needs to be cracked
so if we dont get these two mandatory args we will simply return from the program or if we get path to the file of wordlist is invalid again we will return.
if we get the valid args as well as valid path to the wordlist ,we will proceed with the program execution.
Now we will start iterating over the file and get the words from that file ,
once we read a word from the file we will remove the endline character and then compute hash of that word via crypt method
crypt() -> takes two parameters
1. key - which is the word read from the wordlist
2. salt - two char string chosen from [a-zA-Z0-9./]
if we reach at this point of main function it simply means that wordlist was not enough ,we need more words to compare them.
##Demonstration
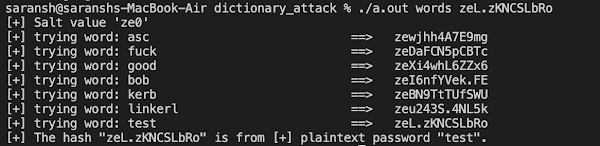
we created sample hash ,with the test program ,this test program is available in the git repo ,link is at end of this page
Now we will run our program explained above where we will pass wordlist file path and hash to be cracked as an arg to this file
As we can see the wordlist contained the word test so we were able to crack the password with the hash only.
Github Repo Path :
Dictionary Attacks
Checkout some more hacking scripts